Information Security Program
The overarching objective of information security is to develop, implement and manage a security program that achieves six basic outcomes of effective security governance:
- Strategic alignment with business strategy to support organizational objectives.
- Execute appropriate risk management measures to protect the confidentiality, integrity, and availability of critical information and systems.
- Optimize security investment for value delivery.
- Develop security architecture(s) to effectively and efficiently manage critical infrastructure resources.
- Monitor and report on information security processes to ensure objectives are achieved.
- Integrate all relevant assurance factors to ensure that processes operate as intended, end-to-end.
Background and Introduction
This document details the Bryant University Information Security Program. It sets forth a university-wide program for evaluating electronic and physical methods of accessing, collecting, storing, using, transmitting and protecting university information assets and technology resources. The goal is consistent delivery across all divisions of the university. This same risk-based Program is applicable to any extension of the campus beyond its Smithfield borders. Adoption of the Program ensures that the university implements and maintains effective information security controls that safeguard valuable university assets (information, people and identities, applications and infrastructure).
Scope
The information security program is designed to promote the protection and ensure the confidentiality, integrity, availability, accountability, and auditability of the university’s information assets. An information security program includes the coordinated set of activities, projects and/or initiatives designed to develop the program, implement the strategy, and manage the outcomes. The objective is to enable the business of the university, students, employees, faculty, partners and customers to carry out teaching and learning, conduct research or business, exchange information and ideas in a secure environment where risk is carefully managed and protection of assets is both comprehensive and pervasive. The program covers all university computing resources and information assets, including but not limited to those managed by administrative staff, university departments, and third-party managed services. The program applies to everyone who uses, maintains or manages university business processes, applications and infrastructure.
Sensitive Data
The University manages sensitive data from many sources including Personally Identifiable Information (PII), accounting, banking and sensitive financial information relating to GLBA, credit card data subject to PCI DSS, and student records subject to FERPA and HIPAA, etc. All this information is in need of protection from unauthorized access and disclosure, which requires a thorough understanding of the nature of the information, where it is located, how it is created, transmitted, shared, stored, deleted and ultimately destroyed. University/business information belongs to whoever is ultimately responsible for the business process.
Security Program Governance and Management
The President’s Cabinet approves the Bryant University Information Security Plan. The Plan sets the direction for information security, program strategy, development, and management at the university.
GOVERNANCE AND MANAGEMENT STRUCTURE
- President’s Cabinet – Establish the program to protect the assets and interests of the university
- The Chief Information Officer (CIO) – ensures that stakeholder needs, conditions and options are evaluated to determine balanced, agreed-on university objectives to be achieved; sets direction through prioritization and decision making
- Cyber Risk Committee – Act on behalf of Cabinet in fulfilling its oversight responsibility
- Information Security Officer – Responsible for designing, implementing and managing the security program in alignment with the direction set by university governance bodies
Risk Definition
Risk is defined as the possibility of suffering harm or loss. Risk = Likelihood x Impact
Cyber Risk Committee Guidance
The Risk Committee should be upholding the goals, objectives, mission and initiatives of the University while adhering to the Cyber Risk Charter. Also, the Risk Committee must have the capability and culture to effectively answer the following questions:
- What are all the risks to our business strategy and operations?
- How much risk are we willing to take?
- How good are we at overseeing risk taking?
- How do we ensure we have the right information to manage risk?
- How do we determine the size and scope of the risks and report the results?
- How well do we manage the risks?
- What are we doing about the risks?
- What else can go wrong and how are risks interconnected?
Risk Process & Activities
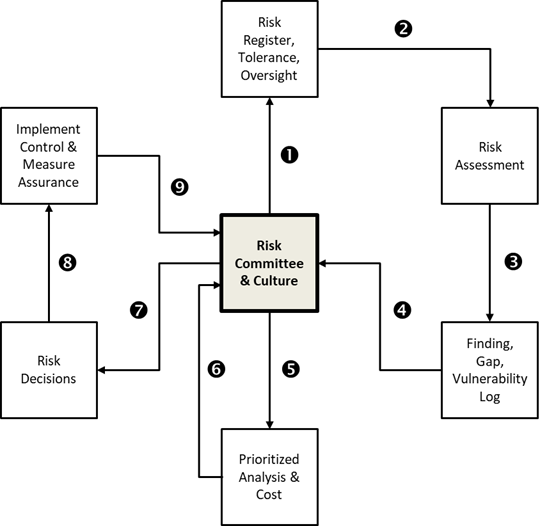
CYBER RISK COMMITTEE CHARTER
View the Cyber Risk Committee Charter.
OBJECTIVES
The Information Security Program Committee serves the following functions:
- Oversight of guidelines and recommendations for implementing the university’s information security policy
- Oversight in the development of standards, guidelines and procedures required to protect the university’s information assets and technology resources
- Serve as a forum for collaboration among the participants to ensure consistent approaches to assessing, mitigating and responding to risks
- Ensure security controls are implemented, maintained and reported
- Facilitate requests to provide information security assurance, metrics and reports
- Bring confidence to our constituents and other interested parties that their information is being protected in accordance with recognized security standards, while at the same time assuring university management that our own proprietary information is being properly protected
Program Coordination
The university employees designated for the coordination and execution of this program are the Information Security Officer (ISO) for the Office of Information Services and representatives from divisional units that serve as the Cyber Risk Committee. The program shall be evaluated periodically, adjusted by Cabinet as necessary in light of relevant circumstances, including changes in the university’s business arrangements or operations.
Guidelines
The Office of Information Services (OIS) will set electronic guidelines for the safeguarding of university information that is in electronic format. The OIS will maintain and provide access to university practices, guidelines and recommendations that are designed to safeguard against anticipated threats to the security or integrity of university information, in either electronic or other formats, and to guard against the unauthorized use of university information. Each relevant university business unit is responsible for securing protected student, financial and educational records located in its unit in accordance with this program and all other university practices and applicable laws. Each relevant university business unit must develop and maintain a plan that details the safeguards and security procedures for information located in its unit. Each relevant university business unit will make its security plan available to the OIS upon request.
Security Program Goals and Objectives
The security program has the following goals:
- Develop a Program implementation roadmap for the university inclusive of all divisions and all university campus extensions. Review and receive approval from the President’s Cabinet and/or Information Security Program Committee (ISPC) for implementing the various components of the Program across all divisions and university extensions based on the roadmap
- Align with industry best practices [ISO 27002:2013, NIST, Critical Security Controls]
- Manage security throughout its life cycle
- Integrate security and compliance into “normal” operations
- Identify/assign/acquire appropriate resources and investments (tools, technology, training, staffing) to implement and maintain the security program
- Develop and communicate a comprehensive security framework which encompasses the following critical asset groups: Cyber-Security, Endpoint Security, Application Security, Network Security, Systems/Datacenter Security, Database Security, Identity and Access Management (IAM) Governance, Data Governance, Critical Business Unit Assets
- Develop and implement a comprehensive communication plan designed to increase general awareness and educate/ advise key stakeholders on security program deliverables, policies, guidelines and recommendations regarding the protection of university assets.
Program Framework
The information security program by large adapts to the National Institute for Standards and Technology (NIST), “Framework for Improving Critical Infrastructure Cybersecurity”, for managing the University’s information assets. The framework is a flexible, risk-based implementation that can be used with a broad array of information security risk management processes. Adapting the framework allows the university to establish a roadmap for reducing risk that reflects university risk management priorities.
The framework provides a common taxonomy and mechanism to:
- Describe the university’s current security posture
- Describe the university’s target (desired) state for security
- Identify and prioritize opportunities for improvement within the context of a continuous and repeatable process
- Assess progress toward the target state
- Communicate risk among internal and external stakeholders
The framework will be implemented over time and scaled in accordance with university priorities within the practical constraints of budget and resources.
Security Program Controls
The security program recognizes the importance of having multiple best practice “guidance systems” to navigate the University’s information security efforts. Therefore, the program promotes a balanced portfolio of management, operational and technical controls using NIST, ISO 27002:2013, and cybersecurity controls from the Critical Security Controls Council on Cyber Security.
Security controls as defined by NIST: “the management, operational, and technical safeguards or countermeasures prescribed for an information system to adequately protect the confidentiality, integrity, and availability of the system and the information it contains.”
Performance Metrics
Assess and, where applicable, measure security program performance and report the results to management for review. Effective security program metrics will be developed based on the following criteria:
- Meaningful – The metric must be understood by the recipients
- Accurate – A reasonable degree of accuracy is essential
- Cost effective – The measurements should not be costly to acquire or maintain
- Repeatable – The measure must be reliable over time
- Predictive – The measurement must be indicative of outcomes
- Actionable – It should be clear to the recipient what action should be taken
- Genuine – Not random or subject to manipulation.
Program Improvement
The following steps will be repeated as necessary to continuously improve the program:
- Assess prioritization and scope of the program
- Orient the program to changing scope, assets, risk approach
- Conduct periodic risk assessments guided by the university’s overall risk management process
- Continue to update the university’s target profile
- Determine, analyze, and prioritize gaps in the program
- Implement new action plans.